Event Id 4670 event is generated when permissions on an object were changed. An object can be a file system, key, folder, registry, Service, or security token object. This event identifies the object, old and new permissions, and who changes the access control list (ACL) for an object.
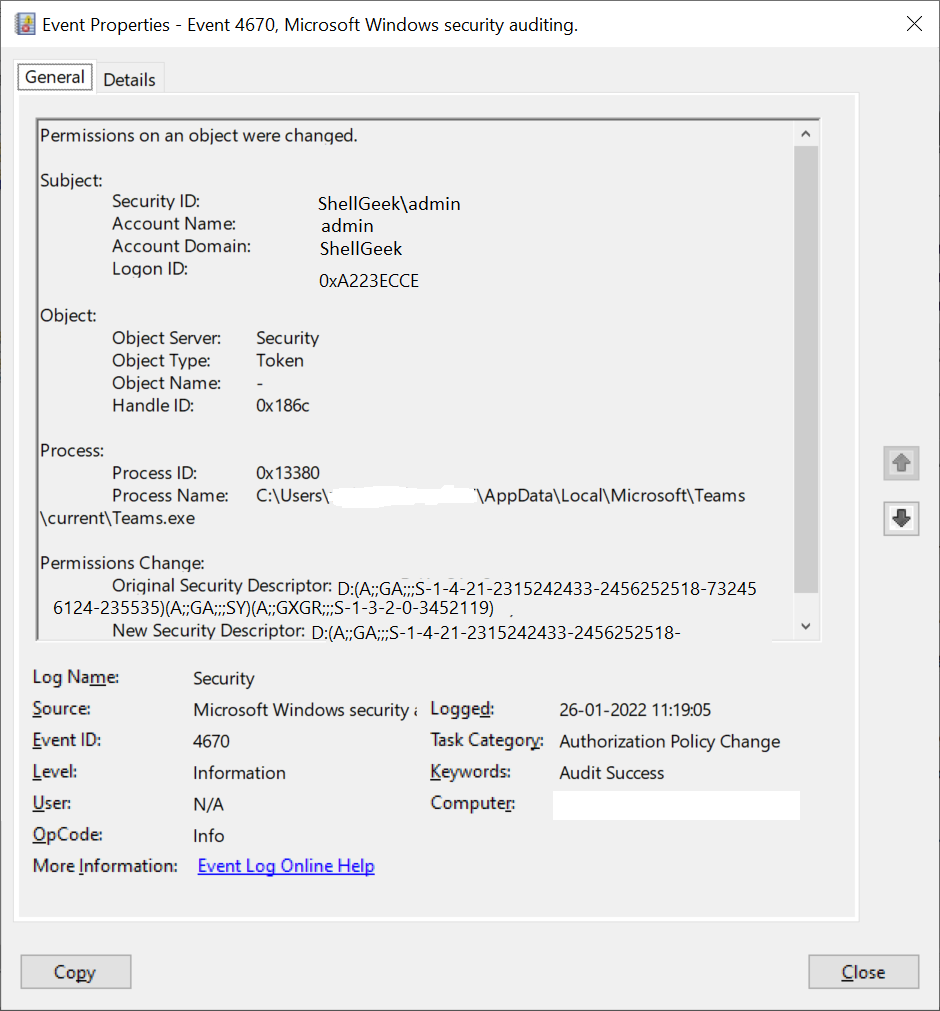
Event Id 4670 is generated when auditing is enabled on an object. Auditing should be enabled on objects audit policy for “Change Permissions” or “Take Ownership“.
For example, to log event 4670 for file system object change, the File system subcategory must be enabled. To log an event for the registry key, “Write DAC” and “Write Owner” must be set in the registry object SACL.
In this article, we will discuss event Id 4670, information about its authorization policy change category, event id 4670 object type token, and its security descriptor.
Event ID 4670 Information
Let’s understand event ID 4634 in detail with its fields.
Event Id 4670 XML format
- <Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
- <System>
<Provider Name="Microsoft-Windows-Security-Auditing" Guid="{62736363-7623-8273-B5CA-2E3C0352D30E}" />
<EventID>4670</EventID>
<Version>0</Version>
<Level>0</Level>
<Task>13570</Task>
<Opcode>0</Opcode>
<Keywords>0x8020000000000000</Keywords>
<TimeCreated SystemTime="2022-01-25T18:10:21.495462300Z" />
<EventRecordID>19764011</EventRecordID>
<Correlation />
<Execution ProcessID="4" ThreadID="14664" />
<Channel>Security</Channel>
<Computer>DC01.ShellGeek.local</Computer>
<Security />
</System>
- <EventData>
<Data Name="SubjectUserSid">S-1-4-21</Data>
<Data Name="SubjectUserName">admin</Data>
<Data Name="SubjectDomainName">SHELLGEEK</Data>
<Data Name="SubjectLogonId">0x1c3bac</Data>
<Data Name="ObjectServer">Security</Data>
<Data Name="ObjectType">Token</Data>
<Data Name="ObjectName"></Data>
<Data Name="HandleId">0xc610</Data>
<Data Name="OldSd">D:(A;;GA;;;S-1-4-21-2315242433-2456252518-732456124-235535)(A;;GA;;;SY)(A;;GXGR;;;S-1-3-2-0-3452119)</Data>
<Data Name="NewSd">D:(A;;GA;;;S-1-4-21-2315242433-2456252518-732456124-235535)(A;;GA;;;SY)</Data>
<Data Name="ProcessId">0xb304</Data>
<Data Name="ProcessName">C:\Users\admin\AppData\Local\Microsoft\Teams\current\Teams.exe</Data>
</EventData>
</Event>Cool Tip: How to convert XML to CSV file in the PowerShell!
Fields Description:
Subject Information
- Security Id: Security ID for an account that requested change object’s permissions” operation.
- Account Name: The name of the account that requested change object’s permissions” operation.
- Account Domain: Domain name
- Logon ID: It is of HexInt64 type. It contains the hexadecimal value which you can use to correlate this event with recent events that may contain the same Logon ID. For example, event Id 4634 – “An account was logged off.”
Object
- Object Server: It has Security value for event code 4670.
- Object Type:It has Unicode String type value. It represents the type of an event that was access during the operation.
Object Name: It is of type Unicode String. It contains the name for an object for which permissions were changed. For file system object, it displays object name as a File path and for Token objects, it displays “-“.
Handle ID: It contains a hexadecimal value for the handle to Object Name. Handle Id helps you to correlate this event with other events that might have the same handle id.
Process
- Process ID: It contains the hexadecimal value for process Id of the process throgh which the permission were changed.Process Id in the operating system uniquely identify an active process. You can use this process id to correlate this event with other events that might have same process id.
- Process Name: It contains the full path of executable for the process.
Permissions Change
- Original Security Descriptor: It contains the old Security Descriptor Defination Language (SDDL) value for the object.
- New Security Descriptor: It contains the new Security Descriptot Defination Language (SDDL) value for the object.
Cool Tip: Event Id 4776 Code 0xc0000234 – Fix to find the source of attempt!
Event ID 4670 object type
Object type for this event represents the type of event that was accessed during the operation.
In the above example, the Object type is Token.
Refer to the list of most used possible values for Object type as per the Microsoft KB article.
| Directory | Event | Timer | Device |
|---|---|---|---|
| Mutant | Type | File | Token |
| Thread | Section | WindowStation | DebugObject |
| FilterCommunicationPort | EventPair | Driver | IoCompletion |
| Controller | SymbolicLink | WmiGuid | Process |
| Profile | Desktop | KeyedEvent | Adapter |
| Key | WaitablePort | Callback | Semaphore |
| Job | Port | FilterConnectionPort | ALPC Port |
Cool Tip: Event Id 4625 Status Code 0xc000006a – Fix to find the source of attempt!
Event Id 4670 Security Descriptor
This event log permission change for an object, like old permission and new permissions and their security descriptor.
It assigns Security Descriptor Definition Language (SDDL) for old and new security descriptor fields.
Refer to the list of mostly used possible values for event id 4670 security descriptor.
| Value | Description | Value | Description |
|---|---|---|---|
| “AO” | Account operators | “PA” | Group Policy administrators |
| “RU” | Alias to allow previous Windows 2000 | “IU” | Interactively logged-on user |
| “AN” | Anonymous logon | “LA” | Local administrator |
| “AU” | Authenticated users | “LG” | Local guest |
| “BA” | Built-in administrators | “LS” | Local service account |
| “BG” | Built-in guests | “SY” | Local system |
| “BO” | Backup operators | “NU” | Network logon user |
| “BU” | Built-in users | “NO” | Network configuration operators |
| “CA” | Certificate server administrators | “NS” | Network service account |
| “CG” | Creator group | “PO” | Printer operators |
| “CO” | Creator owner | “PS” | Personal self |
| “DA” | Domain administrators | “PU” | Power users |
| “DC” | Domain computers | “RS” | RAS servers group |
| “DD” | Domain controllers | “RD” | Terminal server users |
| “DG” | Domain guests | “RE” | Replicator |
| “DU” | Domain users | “RC” | Restricted code |
| “EA” | Enterprise administrators | “SA” | Schema administrators |
| “ED” | Enterprise domain controllers | “SO” | Server operators |
| “WD” | Everyone | “SU” | Service logon user |
Cool Tip: How to manipulate Active Directory UserAccountControl flags in PowerShell!
Conclusion
I hope the above article on windows security Event Id 4670 is helpful to you.
It helps you to monitor the events related to permission on an object that was changed.
You can monitor File objects, registry key objects, or all other specific objects that were changed on the computer using EventId 4670.
Cool Tip: Event Id 4771 – Kerberos pre-authentication failed!
Object types and security descriptor table are from the Microsoft KB article. Refer official Microsoft KB article for more details on these event viewer id 4670 object type, event id 4670 security descriptor.
You can find more topics about PowerShell Active Directory commands and PowerShell basics on the ShellGeek home page.
You can read more on other windows security and system event logs as given: