The error code 0xC000006A does means Account logon with a misspelled or bad password but not necessarily locked out.
The error code 0xC000006D means the cause is either a bad username or authentication information.
These logs with Event Id 4625 log under LogName Security with Audit Failure.
In this article, we will discuss error codes 0xC000006A and 0xC000006D, logon failure reason and event id 4625, and the best possible way to find the source of 4625 Event Id in the Windows Server.
Error Code: 0xc000006a
When the user tries to logon into the window server with the correct username but with a bad password, it displays a login attempt failed message and windows security log event 4625 with error code: 0xc000006a
Logon failure reason for error code 0xc000006a is ‘unknown user name or bad password’.
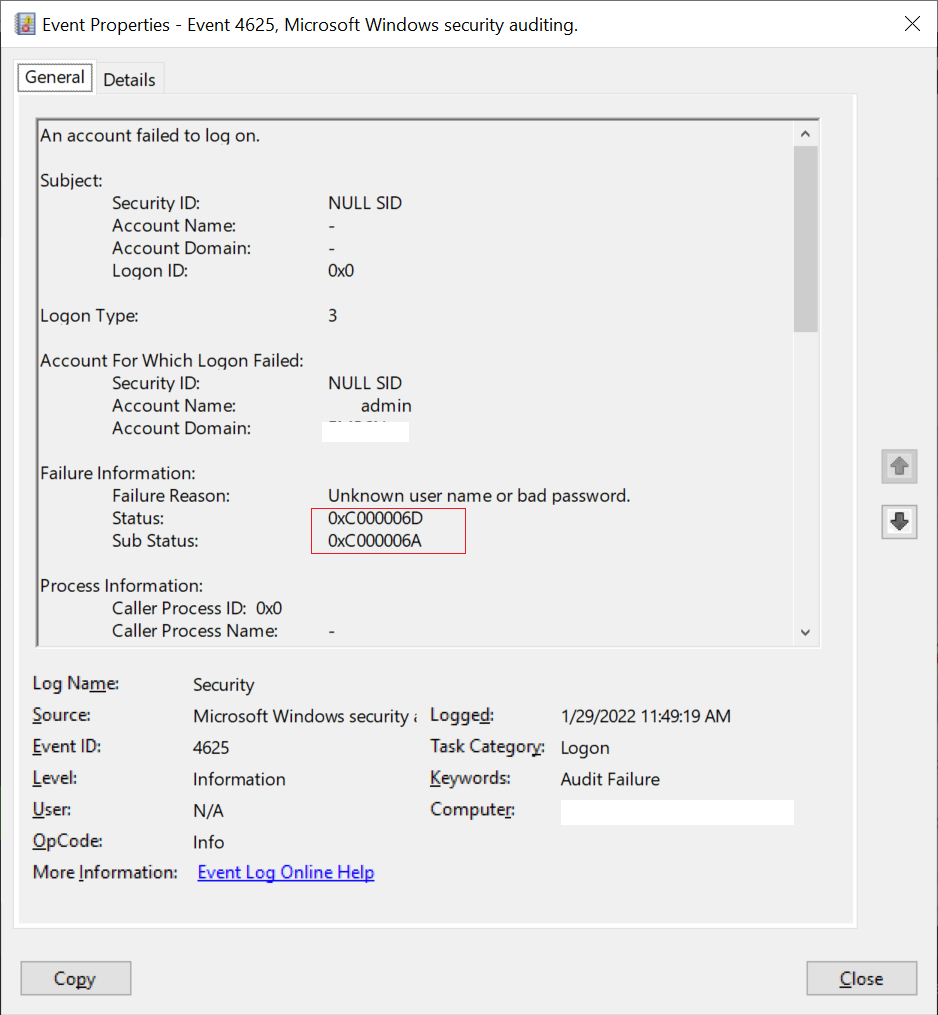
Error Code 0xC000006D
Event Id 4625 contains failure information for error code status 0xC000006D and sub status is 0xC0000064
The failure reason for status code 0xC000006D is an Unknown username or bad password.
Cool Tip: How to perform concatenation of string in PowerShell!
Event Id 4625 Description
Event Id 4625 generates on the workstation where a logon attempt was made.
Failure reason may be an unknown user name or a bad password.
It generates on domain controllers, workstations, and Windows servers.
An account failed to log on.
Subject:
Security ID: NULL SID
Account Name: -
Account Domain: -
Logon ID: 0x0
Logon Type: 3
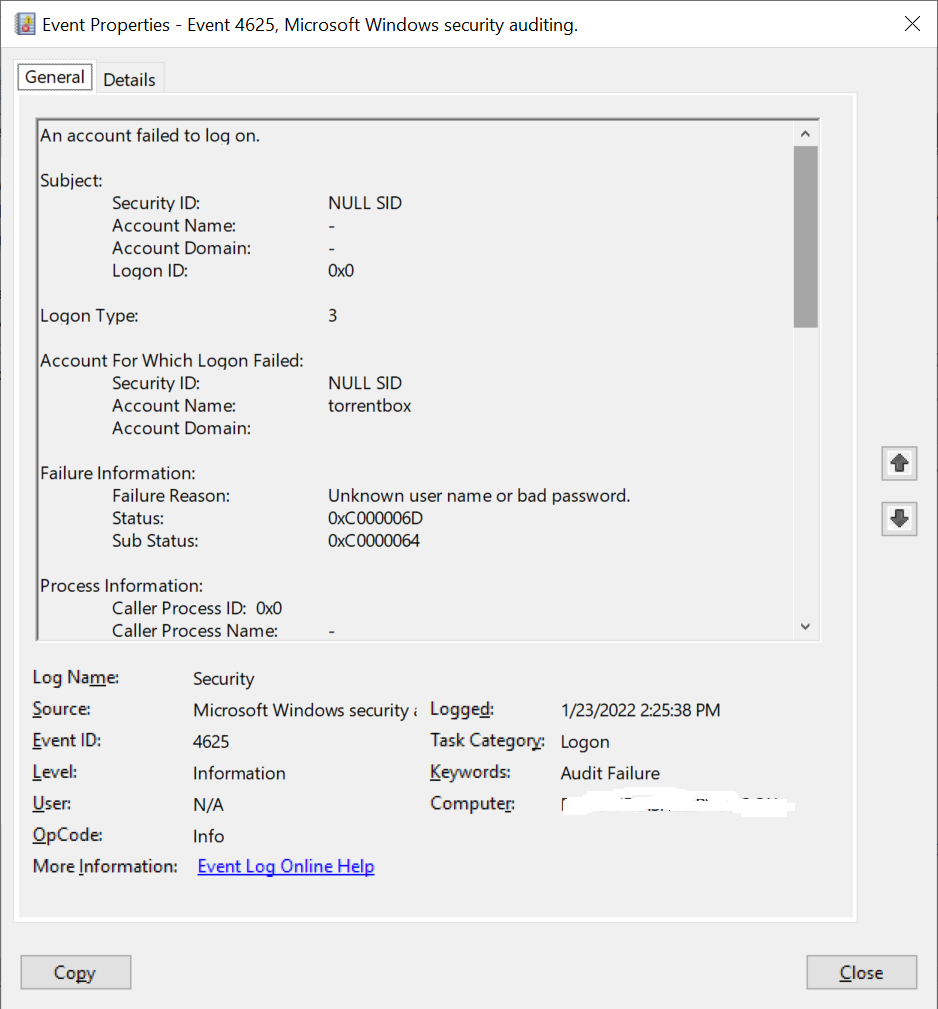
Account For Which Logon Failed:
Security ID: NULL SID
Account Name: torrentbox
Account Domain:
Failure Information:
Failure Reason: Unknown user name or bad password.
Status: 0xC000006D
Sub Status: 0xC0000064
Process Information:
Caller Process ID: 0x0
Caller Process Name: -
Network Information:
Workstation Name: B_21
Source Network Address: **.**.***.160
Source Port: 0
Detailed Authentication Information:
Logon Process: NtLmSsp
Authentication Package: NTLM
Transited Services: -
Package Name (NTLM only): -
Key Length: 0
This event is generated when a logon request fails. It is generated on the computer where access was attempted.
The Subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The Logon Type field indicates the kind of logon that was requested. The most common types are 2 (interactive) and 3 (network).
The Process Information fields indicate which account and process on the system requested the logon.
The Network Information fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The authentication information fields provide detailed information about this specific logon request.
- Transited services indicate which intermediate services have participated in this logon request.
- Package name indicates which sub-protocol was used among the NTLM protocols.
- Key length indicates the length of the generated session key. This will be 0 if no session key was requested.Event Id 4625 provides details about it like Subject Id, Logon type, Account for which Logon failed, Failure Information, Process Information, Network Information, and Detailed Authentication Information.
Cool Tip: Event Id 4634 – An Account was logged off!
Refer Windows Logon Status code table to find the logon failure reason for the Status codes.
| Status\Sub-Status Code | Description |
|---|---|
| 0XC000005E | There are currently no logon servers available to service the logon request. |
| 0xC0000064 | User logon with a misspelled or bad user account |
| 0xC000006A | User logon with misspelled or bad password |
| 0XC000006D | The cause is either a bad username or authentication information |
| 0XC000006E | Indicates a referenced user name and authentication information are valid, but some user account restriction has prevented successful authentication (such as time-of-day restrictions). |
| 0xC000006F | User logon outside authorized hours |
| 0xC0000070 | User logon from unauthorized workstation |
| 0xC0000071 | User logon with expired password |
| 0xC0000072 | User logon to account disabled by administrator |
| 0XC00000DC | Indicates the Sam Server was in the wrong state to perform the desired operation. |
| 0XC0000133 | Clocks between DC and other computer too far out of sync |
| 0XC000015B | The user has not been granted the requested logon type (also called the logon right) at this machine |
| 0XC000018C | The logon request failed because the trust relationship between the primary domain and the trusted domain failed. |
| 0XC0000192 | An attempt was made to logon, but the Netlogon service was not started. |
| 0xC0000193 | User logon with expired account |
| 0XC0000224 | User is required to change password at next logon |
| 0XC0000225 | Evidently a bug in Windows and not a risk |
| 0xC0000234 | User logon with account locked |
| 0XC00002EE | Failure Reason: An Error occurred during Logon |
| 0XC0000413 | Logon Failure: The machine you are logging on to is protected by an authentication firewall. The specified account is not allowed to authenticate to the machine. |
| 0x0 | Status OK. |
Cool Tip: Event Id 4776 Status Code 0xc0000234 – Fix to find the source of attempt!
Solution to find source of 4625 Event Id Status Code 0xC000006D or 0xC000006A
To know the source of the login attempt, we have to enable verbose netlogon logging on Domain Controller.
- Open a Cmd (Command Prompt) with Administrator privileges.
- Run below command
Nltest /DBFlag:2080FFFF
- Netlogon service stops and restarts are not required.
- If you want to turn off the verbose netlogon logging after the trace of the 4625 event id, run the below command
Nltest /DBFlag:0x0
- Netlogon related events are available in file %windir%\debug\netlogon.log
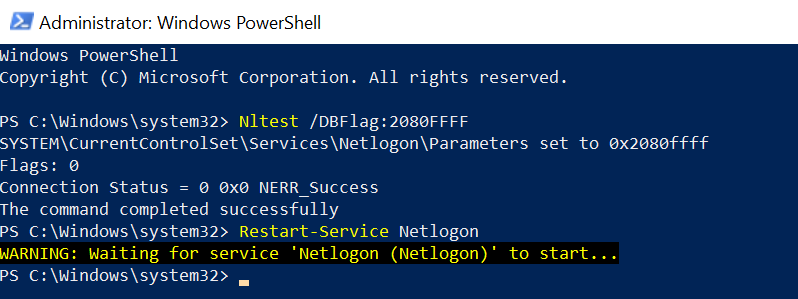
You can run the Nltest command in PowerShell.
Open PowerShell with ‘Run as Administrator and run the below command
Nltest /DBFlag:2080FFFF Restart-Service Netlogon
The output of the enabling verbose log on the workstation is:
To read the events of the above file, open the log file with run as administrator.
netlogon.log file contains the user logon attempt and its source location.
Cool Tip: Event Id 4771 – Kerberos pre-authentication failed!
This will help you to trace the workstation from where the login attempt was coming.
You can enable or disable netlogon logging using the registry method.
- Open the registry editor
- If the Reg_SZ value for the below registry entry exists, delete it.
- Create REG_DWORD with the same word and assign value 2080FFFF hexadecimal value. HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters\DBFlag
Review netogon.log file to display source information like its machine name or IP address.
01/23 15:19:56 [MISC] [5788] SHELL_ENG: DsGetDcName function returns 0 (client PID=704): Dom:SHELL_ENG Acct:(null) Flags: DS NETBIOS RET_DNS
01/23 15:20:12 [LOGON] [4084] SHELL_ENG: SamLogon: Network logon of braceit from CORP-EU-S21 Entered
01/23 15:20:12 [LOGON] [4084] SHELL_ENG: NlPickDomainWithAccount: braceit: Algorithm entered. UPN:0 Sam:1 Exp:0 Cross: 0 Root:1 DC:0
01/23 15:20:12 [LOGON] [4084] SHELL_ENG: SamLogon: Network logon of braceit from CORP-EU-S21 Returns 0xC000006A
01/23 15:20:20 [LOGON] [4084] SHELL_ENG: SamLogon: Network logon of braceit from CORP-EU-S21 Entered
01/23 15:20:20 [LOGON] [4084] SHELL_ENG: NlPickDomainWithAccount: braceit: Algorithm entered. UPN:0 Sam:1 Exp:0 Cross: 0 Root:1 DC:0
01/23 15:20:20 [LOGON] [4084] SHELL_ENG: SamLogon: Network logon of braceit from COPR-EU-S17 Returns 0xC000006A
01/23 15:20:44 [LOGON] [4084] SHELL_ENG: SamLogon: Network logon of braceit from CORP-EU-S21 Entered
01/23 15:20:44 [LOGON] [4084] SHELL_ENG: NlPickDomainWithAccount: braceit: Algorithm entered. UPN:0 Sam:1 Exp:0 Cross: 0 Root:1 DC:0
01/23 15:20:44 [LOGON] [4084] SHELL_ENG: SamLogon: Network logon of braceit from CORP-EU-S21 Returns 0x0
01/23 15:20:47 [LOGON] [4084] SHELL_ENG: SamLogon: Network logon of braceit from CORP-EU-S21 Entered
01/23 15:20:47 [LOGON] [4084] SHELL_ENG: NlPickDomainWithAccount: braceit: Algorithm entered. UPN:0 Sam:1 Exp:0 Cross: 0 Root:1 DC:0
01/23 15:20:47 [LOGON] [4084] SHELL_ENG: SamLogon: Network logon of braceit from CORP-EU-S21 Returns 0x0The above netlogon.log file, it displays the source from where the logon attempt occurred.
This event also logs error code: 0xC000006A, which means the user logon with a misspelled or bad password.
Cool Tip: How to manipulate Active Directory UserAccountControl flags in PowerShell!
If you open Event Id 4625 and look at the details section, it will display the source from where the logon attempt was made.
An account failed to log on.
Subject:
Security ID: NULL SID
Account Name: -
Account Domain: -
Logon ID: 0x0
Logon Type: 3
Account For Which Logon Failed:
Security ID: NULL SID
Account Name: braceit
Account Domain: SHELLGEEK
Failure Information:
Failure Reason: Unknown user name or bad password.
Status: 0xC000006D
Sub Status: 0xC000006A
Process Information:
Caller Process ID: 0x0
Caller Process Name: -
Network Information:
Workstation Name: CORP-EU-S21
Source Network Address: 10.16.15.14
Source Port: 0
Detailed Authentication Information:
Logon Process: NtLmSsp
Authentication Package: NTLM
Transited Services: -
Package Name (NTLM only): -
Key Length: 0
In the above log, it captured the workstation name and source network IP address from where logon attempt was made.
In the failure information field, it logs this event with logon failure reason, error status: 0xC000006D, and sub status: 0xc000006a.
Cool Tip: Event Id 4670 – Permissions on an object were changed!
Conclusion
I hope the above article on error status code 0xc000006a or 0xc000006d logs under windows security event id 4625 is helpful to you.
Error code 0xc000006a means ‘Account logon with a misspelled or bad password but not necessarily locked out.’
Error status code 0xc000006d ‘means ‘The cause is either a bad username or authentication information
Using enabling the verbose logging for the netlogon service on the Domain controller will help you to find out the logon attempt location.
You can find more topics about PowerShell Active Directory commands and PowerShell basics on the ShellGeek home page.
You can read more on other windows security and system event logs as given: