Event Id 4634 event is generated when a logon session is terminated or is destroyed. The session is no longer exists.
When the user initiated the logoff procedure, you will see both Event Id 4647 and 4634.
The main difference between Event Id 4647 vs 4634 is that event id 4647 is generated when a user-initiated the logoff procedure using the logoff function, and event id 4634 is generated when a logon session is terminated and no longer exists.
Event Id 4634 may be positively correlated with Event Id 4624: An account was successfully logged on”. Event using the Login ID value.
Event Id 4634 logon type 2 means user logon to this computer.
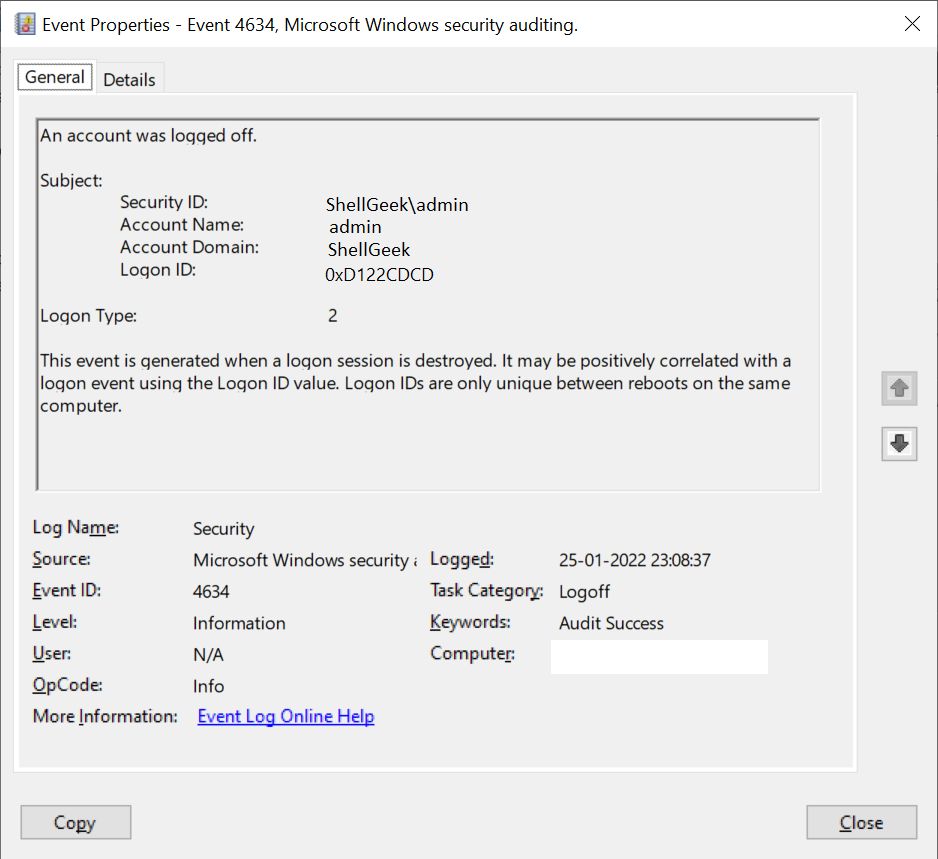
In this article, we will discuss event Id 4634, information about event ID 4634, event id 4634 remote desktop (RDP) session terminated, event id 4634 logon types like 2,3,5,7 and 10.
Event ID 4634 Information
Let’s understand event ID 4634 in detail with its fields.
Event Id 4634 XML format
- <Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
- <System>
<Provider Name="Microsoft-Windows-Security-Auditing" Guid="{62736363-7623-8273-B5CA-2E3C0352D30E}" />
<EventID>4634</EventID>
<Version>0</Version>
<Level>0</Level>
<Task>14339</Task>
<Opcode>0</Opcode>
<Keywords>0x8010000000000000</Keywords>
<TimeCreated SystemTime="2022-01-22T18:10:21.495462300Z" />
<EventRecordID>16708</EventRecordID>
<Correlation />
<Execution ProcessID="520" ThreadID="1084" />
<Channel>Security</Channel>
<Computer>DC01.ShellGeek.local</Computer>
<Security />
</System>
- <EventData>
<Data Name="TargetUserName">admin</Data>
<Data Name="TargetUserSid">S-1-4-21</Data>
<Data Name="TargetDomainName">SHELLGEEK</Data>
<Data Name="TargetLogonId">0xd34ccae7</Data>
<Data Name="LogonType">2</Data>
</EventData>
</Event>Cool Tip: How to convert XML to CSV file in the PowerShell!
Fields Description:
Subject Information
- Security Id: Security ID for an account that was logged off.
- Account Name: The name of the account that was logged off.
- Account Domain: Domain name
- Logon ID: It is of HexInt64 type. It contains the hexadecimal value which you can use to correlate event id 4634 with a recent event that may contain the same Logon ID. For example, event Id 4624 – “An account was succssfully logged on.”
- LogonType: It contains value of type UInt32 to represent the type of logon which was used.
Cool Tip: Event Id 4771 – Kerberos pre-authentication failed!
The Logon Type table shows all possible values for this field.
| Logon Type | Logon Title | Description |
|---|---|---|
| 2 | Interactive | A user logged on to this computer. |
| 3 | Network | A user or computer logged on to this computer from the network. |
| 4 | Batch | Batch logon type is used by batch servers, where processes may be executing on behalf of a user without their direct intervention. |
| 5 | Service | A service was started by the Service Control Manager. |
| 7 | Unlock | This workstation was unlocked. |
| 8 | NetworkCleartext | A user logged on to this computer from the network. The user’s password was passed to the authentication package in its unhashed form. The built-in authentication packages all hash credentials before sending them across the network. The credentials do not traverse the network in plaintext (also called cleartext). |
| 9 | NewCredentials | A caller cloned its current token and specified new credentials for outbound connections. The new logon session has the same local identity but uses different credentials for other network connections. |
| 10 | RemoteInteractive | A user logged on to this computer remotely using Terminal Services or Remote Desktop. |
| 11 | CachedInteractive | A user logged on to this computer with network credentials that were stored locally on the computer. The domain controller was not contacted to verify the credentials. |
Cool Tip: Event Id 4776 Code 0xc0000234 – Fix to find the source of attempt!
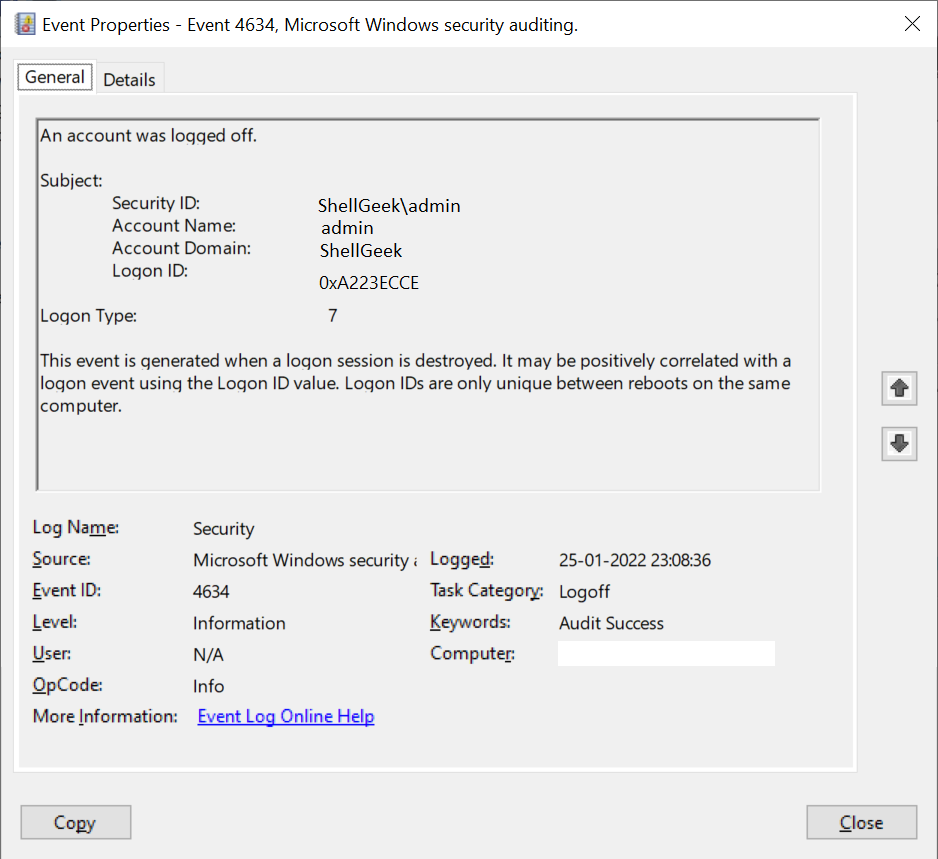
Event Id 4634 logon type 7
When the user unlocks the previously locked workstation, it logs the event id 4634 logon type 7 event.
When the user unlocks the previously locked workstation, it logs the event id 4634 logon type 7 event.
Cool Tip: How to manipulate Active Directory UserAccountControl flags in PowerShell!
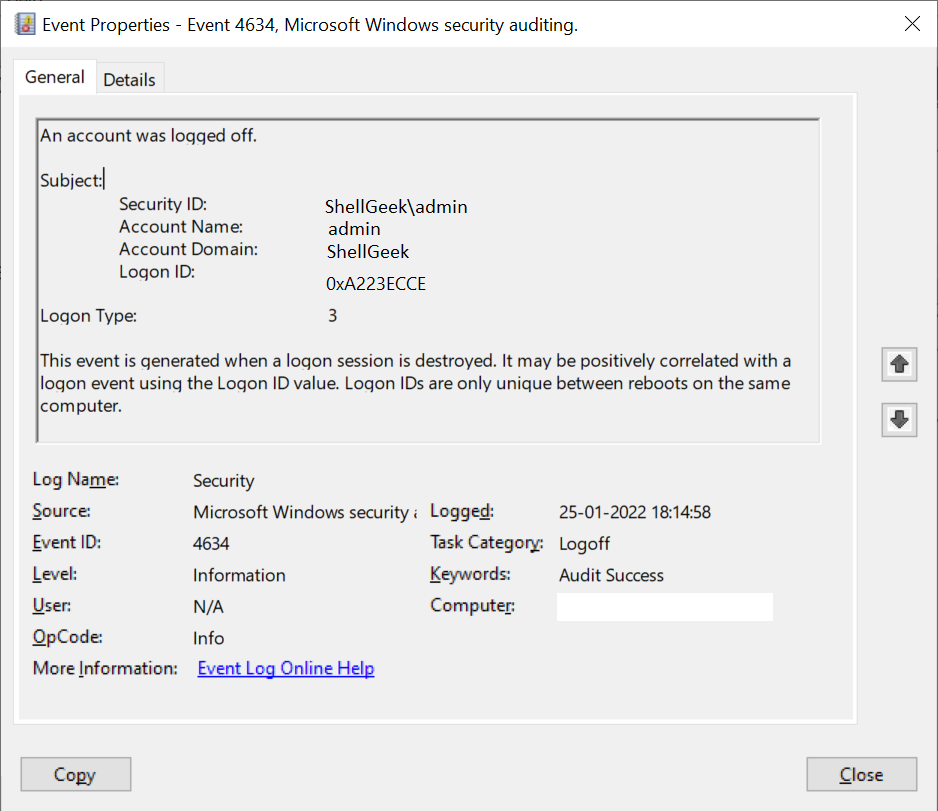
Event Id 4634 logon type 3
Event Id 4634 logon type 3 means that the user or computer logged on to this computer from the network.
The user or computer accesses the computer from the network or tries to access shared resources on the computer, it logs the event id 4634 logon type 3 event.
Cool Tip: Event Id 4625 Status Code 0xc000006a – Fix to find the source of attempt!
Conclusion
I hope the above article on Event Id 4634: “An account was logged off” is helpful to you.
Event Id 4634 helps you to monitor the events related to logon attempts, logged off, remote desktop activities from the network.
Cool Tip: Event Id 4670 – Permissions on an object were changed!
Different types of Event Id 4634 logon type like logon type 2, logon type 3, logon type 7, logon type 10 provides detailed description about the event.
This article is using logon types as per the official Microsoft KB article. Refer for more details on these logon types.
You can find more topics about PowerShell Active Directory commands and PowerShell basics on the ShellGeek home page.
You can read more on other windows security and system event logs as given: