Event Id 4624 is generated when a user logon successfully to the computer. This event was written on the computer where an account was successfully logged on or a session created.
Event Id 4624 logon type specifies the type of logon session created. The most commonly used logon types for this event are 2 – interactive logon and 3 – network logon.
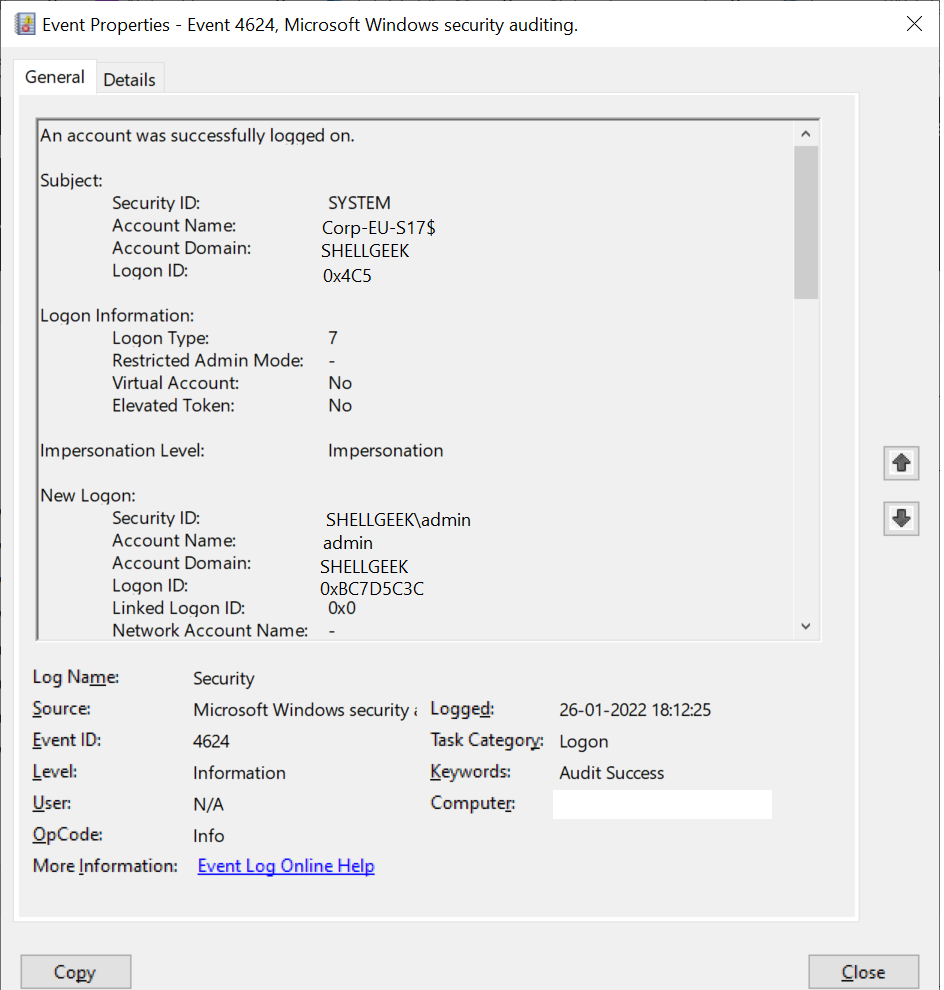
This event logs on the account logged on, It helps to monitor actions on the computer like anomalies or malicious actions, non-active account login attempts, external accounts and so many others.
In this article, we will discuss Windows event id 4624 logon types, event field information, and security monitoring recommendations.
Event Id 4624 – Description
Event code 4624 provides detailed information about an account, logon information, network, and detailed authentication information.
This event is generated on domain controllers (DC), workstations, and systems.
An account was successfully logged on.
Subject:
Security ID: SYSTEM
Account Name: Corp-EU-S17$
Account Domain: SHELLGEEK
Logon ID: 0x4C5
Logon Information:
Logon Type: 7
Restricted Admin Mode: -
Virtual Account: No
Elevated Token: No
Impersonation Level: Impersonation
New Logon:
Security ID: SHELLGEEK\admin
Account Name: admin
Account Domain: SHELLGEEK
Logon ID: 0xBC7D5C3C
Linked Logon ID: 0x0
Network Account Name: -
Network Account Domain: -
Logon GUID: {00000000-0000-0000-0000-000000000000}
Process Information:
Process ID: 0x438
Process Name: C:\Windows\System32\lsass.exe
Network Information:
Workstation Name: Corp-EU-S17
Source Network Address: -
Source Port: -
Detailed Authentication Information:
Logon Process: Negotiate
Authentication Package: Negotiate
Transited Services: -
Package Name (NTLM only):-
Key Length: 0
This event is generated when a logon session is created. It is generated on the computer that was accessed.
The subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The logon type field indicates the kind of logon that occurred. The most common types are 2 (interactive) and 3 (network).
The New Logon fields indicate the account for whom the new logon was created, i.e. the account that was logged on.
The network fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The impersonation level field indicates the extent to which a process in the logon session can impersonate.
The authentication information fields provide detailed information about this specific logon request.
- Logon GUID is a unique identifier that can be used to correlate this event with a KDC event.
- Transited services indicate which intermediate services have participated in this logon request.
- Package name indicates which sub-protocol was used among the NTLM protocols.
- Key length indicates the length of the generated session key. This will be 0 if no session key was requested.Fields Description:
Subject:
- Security ID: SID of an account
- Account Name: It specifies the name of the account.
- Account Domain: Computer domain or subject domain name.
- Logon ID: hexadecimal number which helps you to correlate this event ID 4624 with a recent event that might contain the same Logon ID. For ex. Event code 4634: “An account was logged off”
Logon Information
- Logon Type: It provides an integer value that provides information about the type of logon occured on the computer.
- Restricted Admin Mode: It provides value if RemoteInteractive logon type sessions occur. It contains the Yes/No flag value which indicates if the credentials used during the RDP session using Restricted Admin mode. If it is not RemoteInteractive logon, this field will display a “-” string.
- Virtual Account: It provides the Yes or No flag value which indicates if the account is a virtual account.
- Elevated Token: It provides the Yes or No flag value. If it has a Yes value, it means the created logon session is elevated and has administrator privileges.
Impersonation Level
Impersonation level can have one of these value
- SecurityAnonynymous: displayed as an empty string. The server process cannot object identification information about the client and cannot impersonate the client.
- SecurityIdentification: displayed as “Identification”. The server process can obtain information about the client, but it cannot impersonate the client.
- SecurityImpersonation: displayed as “Impersonation“. The server process can impersonate the client’s information. This is the most common type.
- SecurityDelegation: displayed as “Delegation“. The server process can impersonate the client information on a remote system.
New Logon
- Security ID: SID of an account for which logon was occured.
- Account Name: The name of an account for which logon was occured.
- Account Domain: The computer domain name or subject’s domain name.
- Logon ID: Hexadecimal value which helps you to correlate the recent events that might contain the same Logon Id.
- Linked Logon ID: Hexadecimal value of the paired session.
- Network Account Name: It provides a domain for the user and value for NewCredentials logon type. Mostly its value is “-“.
- Logon GUID: It provides a GUID that can help you to correlate this Windows event id 4624 with another event that might contain the same Logon GUID.
Process Information
- Process ID: Process id is the process that attempted logon.
- Process Name: Full path and name of executable for the process.
Network Information
- Workstation Name: computer name from which logon attempt was occurred.
- Source Network Address: IP address of a machine from which logon attempt was performed.
- Source Port: Source port of machine from which logon attempt was occured.
Detailed Authentication Information:
- Logon Process: It specifies the trusted logon process that was used for logon.
- Authentication Package: It specifies the name of authentication package that was used for logon authentication process.
- Transited Services: The list of transmitted services.
- Package Name: The name of the LAN manager sub-package which was used during logon.
- Key Length: The length of the NTLM session security key.
Cool Tip: How to manipulate Active Directory UserAccountControl flags in PowerShell!
Event ID 4624 logon types
The Logon type is of type Int32. It specifies the type of logon which was occurred.
Refer to the list of event code 4624 logon types with a logon title and their description.
| Logon Type | Logon Title | Description |
|---|---|---|
0 | System | Used only by the System account, for example at system startup. |
2 | Interactive | A user logged on to this computer. |
3 | Network | A user or computer logged on to this computer from the network. |
4 | Batch | Batch logon type is used by batch servers, where processes may be executing on behalf of a user without their direct intervention. |
5 | Service | A service was started by the Service Control Manager. |
7 | Unlock | This workstation was unlocked. |
8 | NetworkCleartext | A user logged on to this computer from the network. The user’s password was passed to the authentication package in its unhashed form. The built-in authentication packages all hash credentials before sending them across the network. The credentials do not traverse the network in plaintext (also called cleartext). |
9 | NewCredentials | A caller cloned its current token and specified new credentials for outbound connections. The new logon session has the same local identity, but uses different credentials for other network connections. |
10 | RemoteInteractive | A user logged on to this computer remotely using Terminal Services or Remote Desktop. |
11 | CachedInteractive | A user logged on to this computer with network credentials that were stored locally on the computer. The domain controller was not contacted to verify the credentials. |
12 | CachedRemoteInteractive | Same as RemoteInteractive. This is used for internal auditing. |
13 | CachedUnlock | Workstation logon. |
Get Event log for Event Id 4624 using PowerShell
You can retrieve the event logs for event id 4624 using PowerShell cmdlets like Get-EventLog or Get-WinEvent
Let’s try to get event id 4624 event log using Get-EventLog cmdlet in PowerShell.
$Date = [DateTime]::Now.AddDays(-1)
Get-EventLog -LogName "Security" -After $Date | Where -FilterScript {$_.EventID -eq 4624}
In the above script,
Get-EventLog gets event id 4624 logs for a date using the $Date variable.
It uses the LogName parameter to specify the log name as Security for this event and the Event Id is equal to 4624.
The output of the above Get-EventLog to get this event id log is
Index Time EntryType Source InstanceID Message
----- ---- --------- ------ ---------- -------
20033758 Jan 26 22:04 SuccessA... Microsoft-Windows... 4624 An account was successfully logged on....
20033006 Jan 26 21:49 SuccessA... Microsoft-Windows... 4624 An account was successfully logged on....
20032288 Jan 26 21:34 SuccessA... Microsoft-Windows... 4624 An account was successfully logged on....
20031576 Jan 26 21:19 SuccessA... Microsoft-Windows... 4624 An account was successfully logged on....
20031572 Jan 26 21:19 SuccessA... Microsoft-Windows... 4624 An account was successfully logged on....
20031303 Jan 26 21:14 SuccessA... Microsoft-Windows... 4624 An account was successfully logged on....You can also get event logs for event code 4624 using the Get-WinEvent cmdlet in PowerShell.
Get-WinEvent -FilterHashtable @{LogName = 'Security'; ID = 4624} -MaxEvents 10
In the above PowerShell script,
Get-WinEvent gets event log for event id 4624.
It uses the FilterHashtable parameter and LogName as Security to get these events.
The output of the above command is:
ProviderName: Microsoft-Windows-Security-Auditing
TimeCreated Id LevelDisplayName Message
----------- -- ---------------- -------
26-01-2022 22:04:21 4624 Information An account was successfully logged on....
26-01-2022 21:49:21 4624 Information An account was successfully logged on....
26-01-2022 21:34:21 4624 Information An account was successfully logged on....
26-01-2022 21:19:57 4624 Information An account was successfully logged on....
26-01-2022 21:19:54 4624 Information An account was successfully logged on....
26-01-2022 21:14:27 4624 Information An account was successfully logged on....
26-01-2022 21:07:51 4624 Information An account was successfully logged on....
26-01-2022 20:50:07 4624 Information An account was successfully logged on....
26-01-2022 20:45:50 4624 Information An account was successfully logged on....
26-01-2022 20:36:21 4624 Information An account was successfully logged on....Window Security Event Id 4624 – Examples
Event Code 4624 logon type 5 – Service started by SCM
Event Id 4624 logon type 5 logs message when the service was started by the Service Control Manager (SCM).
An account was successfully logged on.
Subject:
Security ID: SYSTEM
Account Name: Corp-EU-S17$
Account Domain: SHELLGEEK
Logon ID: 0x3E7
Logon Information:
Logon Type: 5
Restricted Admin Mode: -
Virtual Account: No
Elevated Token: Yes
Impersonation Level: Impersonation
New Logon:
Security ID: SYSTEM
Account Name: SYSTEM
Account Domain: NT AUTHORITY
Logon ID: 0x3E7
Linked Logon ID: 0x0
Network Account Name: -
Network Account Domain: -
Logon GUID: {00000000-0000-0000-0000-000000000000}
Process Information:
Process ID: 0x41c
Process Name: C:\Windows\System32\services.exe
Network Information:
Workstation Name: -
Source Network Address: -
Source Port: -
Detailed Authentication Information:
Logon Process: Advapi
Authentication Package: Negotiate
Transited Services: -
Package Name (NTLM only): -
Key Length: 0
This event is generated when a logon session is created. It is generated on the computer that was accessed.
The subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon.exe or Services.exe.
The logon type field indicates the kind of logon that occurred. The most common types are 2 (interactive) and 3 (network).
The New Logon fields indicate the account for whom the new logon was created, i.e. the account that was logged on.
The network fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases.
The impersonation level field indicates the extent to which a process in the logon session can impersonate.
The authentication information fields provide detailed information about this specific logon request.
- Logon GUID is a unique identifier that can be used to correlate this event with a KDC event.
- Transited services indicate which intermediate services have participated in this logon request.
- Package name indicates which sub-protocol was used among the NTLM protocols.
- Key length indicates the length of the generated session key. This will be 0 if no session key was requested.Event Id 4624 displays the logon process name as Advapi which was used for logon.
Conclusion
I hope the above article on Event Id 4624 is useful to you.
This event helps you to monitor the type of account logon activity on the computer system.
Using Event Code 4624, you can monitor high-value accounts, anomalies, or malicious actions on the computer using New log on \Security Id to monitor how and when a particular account is being used.
Cool Tip: Event Id 4771 – Kerberos pre-authentication failed!
You can find more topics about PowerShell Active Directory commands and PowerShell basics on the ShellGeek home page.
You can read more on other Windows security and system event logs as given: