Get-AdDomainController cmdlet in PowerShell is used to get a list of domain controllers in the Active Directory.
The Get-AdDomainController gets the domain controller specified by the Identity, Filter, or Discover parameter. There are other ways to get a list of domain controllers in a domain using Get-ADGroupMember, and Get-AdForest cmdlet in PowerShell.
In this article, I will show you how to get all domain controllers using the Get-AdDomainController cmdlet in PowerShell.
List all Domain Controllers in the Domain
To get a list of domain controllers in the domain use the Get-AdDomainController cmdlet in PowerShell.
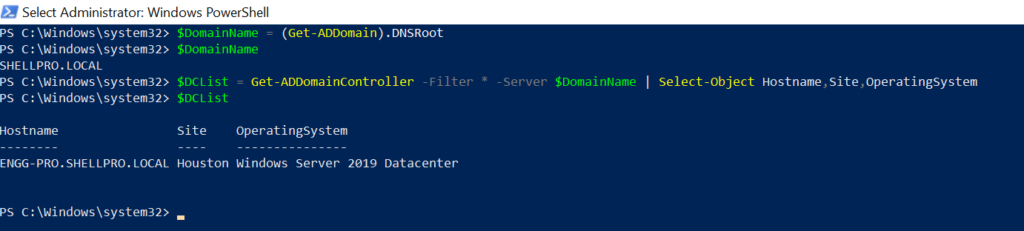
$DomainName = (Get-ADDomain).DNSRoot $DCList = Get-ADDomainController -Filter * -Server $DomainName | Select-Object Hostname,Site,OperatingSystem
In the above PowerShell script, the Get-AdDomain PowerShell cmdlet gets the AD domain name and stores it in the variable $DomainName.
The second command, the Get-AdDomainController cmdlet uses the Server parameter to list all domain controllers in the specified domain name and pass the object to select HostName, Site, and OperatingSystem properties.
The output of the above script to get all domain controllers is given below.
Get all Domain Controllers using Get-AdGroupMember
You can use the Get-AdGroupMember cmdlet in PowerShell to get all domain controllers in the domain.
Get-ADGroupMember 'Domain Controllers'
This command uses the Get-AdGroupMember cmdlet to get all domain controllers, output is given below.
distinguishedName : CN=ENGG-PRO,OU=Domain Controllers,DC=SHELLPRO,DC=LOCAL
name : ENGG-PRO
objectClass : computer
objectGUID : dbf93c91-4f31-401e-b924-88cfed6b16c0
SamAccountName : ENGG-PRO$
SID : S-1-5-21-1426734019-4042446242-464921959-1000List all Domain Controllers in the Forest
You can use the Get-AdForest cmdlet in PowerShell to list all domain controllers for all domains in a forest.
$DCList = (Get-ADForest).Domains | %{ Get-ADDomainController -Filter * -Server $_ }
In the above PowerShell script, the Get-AdForest cmdlet gets all domains in a forest and passes the output to the second command.
The second command uses Get-AdDomainController to list all domain controllers for all domains in a forest.
Nltest to list all Domain Controllers
Nltest is a command-line tool used to list all domain controllers in a domain.
Run below command below.
nltest /dclist:SHELLPRO.LOCAL
This command gets all domain controllers in the domain name SHELLPRO.LOCAL
Cool Tip: How to check FSMO role holders using PowerShell!
Conclusion
I hope the above article on how to list all domain controllers in the domain is helpful to you.
Get-AdDomainController cmdlet in PowerShell is used to get a list of domain controllers, and IP information. You can use other commands like Get-AdForest, nltest to list all domain controllers.
Cool Tip: How to use get-adprincipalgroupmembership in Active Directory!
You can find more topics about PowerShell Active Directory commands and PowerShell basics on the ShellGeek home page.