The dsquery command-line tool is used to find the objects in the active directory according to the specified search criteria using the LDAP query.
Use dsquery with filter parameter to get user last logon to the computer in the active directory.
The lastlogon timestamp is the time the user last logged into the domain. The user’s last logon timestamp value is stored as a large integer in the Domain controller (DC). This date timestamp value represents the number of 100-nanosecond intervals since January 1, 1601 (UTC).
Use the LDAP query in the LDAP search filter format to specify the -filter parameter to retrieve user lastlogon and lastlogontimestamp.
In this tutorial, we will learn how to use dsquery to get user last logon and lastlogontimestamp in PowerShell.
Using dsquery to get user last logon
Use the dsquery command-line tool to find any objects and their attributes like lastlogon, and lastlogontimestamp in the active directory according to search criteria.
dsquery * -filter "samaccountname=admin" -attr samaccountname lastlogon
In the above query, to get user lastlogon to the computer, we have specified the search criteria in the filter parameter as "samaccountname = admin".
Using the dsquery * command, it finds the user lastlogon, and using the -attr parameter to display attributes name, it displays attributes samaccountname and user lastlogon.
The output of the above dsquery to get user’s last logon is:
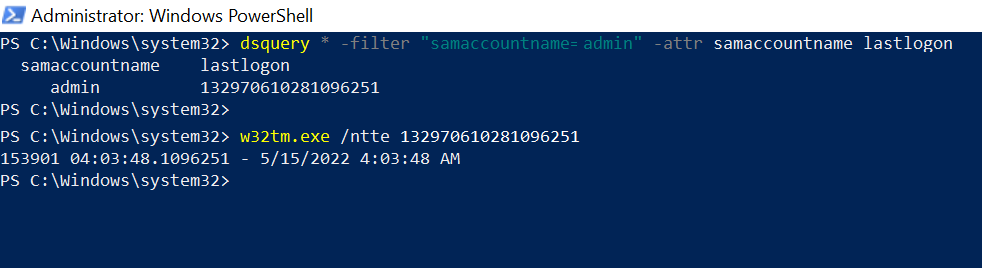
When the user logged into the domain, it stored its lastlogon value as a large integer and not in a human-readable format.
To convert lastlogon to date, we have used the w32tm.exe tool with /ntte which converts a Network Time Protocol (NTP) time into a readable format.
Cool Tip: Difference between lastlogon and lastlogontimestamp in the Active Directory!
Find user lastlogontimestamp using the dsquery
Domain Controller (DC) checks the user lastlogontimestamp attribute value when the user logged into the domain. LastLogonTimestamp value is replicated, by default if its value is 14 days or older than the previous value.
Using the dsquery command-line tool, we can retrieve the user lastlogontimestamp attribute.
dsquery * -filter "samaccountname=admin" -attr samaccountname lastlogon lastlogontimestamp
In the above PowerShell script, dsquery uses a filter parameter to specify the search criteria to search for user and get its attributes lists like samaccountname, lastlogon, and user lastlogontimestamp.
The output of the above query to find user lastlogontimestamp using the dsquery is:
PS C:\Windows\system32> dsquery * -filter "samaccountname=admin" -attr samaccountname lastlogon lastlogontimestamp
samaccountname lastlogon lastlogontimestamp
admin 132970610281096251 132968489843663168Use the w32tm.exe command-line tool with /ntte parameter to convert user lastlogontimestamp to DateTime ( human-readable format).
PS C:\Windows\system32> w32tm.exe /ntte 132970610281096251
153901 04:03:48.1096251 - 5/15/2022 4:03:48 AM
PS C:\Windows\system32> w32tm.exe /ntte 132968489843663168
153898 17:09:44.3663168 - 5/12/2022 5:09:44 PMConclusion
I hope the above article on how to use dsquery to get user lastlogon and user lastlogontimestamp is helpful to you.
Use w32tm.exe /ntte command-line tool to convert lastlogon and lastlogontimestamp to date format ( human-readable format).
You can find more topics about PowerShell Active Directory commands and PowerShell basics on the ShellGeek home page.